DNSBL Server
DNSBL Concepts
What is a DNSBL?
A DNSBL, DNS Black(or Block) List server is simply a DNS server used to determine if an IPv4 address has a record, "is listed", in a blocklist server's domain. A DNSBL is used as a second (assuming the firewall is the first) defense check used to determine if a sending server should be prohibited from connecting to your email server.
Typical IP addresses listed in a DNSBL
- Known Repeat Spam sources
- Commercial ISP DHCP address ranges whose customers should be using the ISP's email services
- Rogue IP addresses that are unregistered
Why Would a Company Want its Own DNSBL?
Good question! There are free, public, DNSBLs, so why have your own?
- There are unlisted bad guys sending spam or malware to your company
- Your company receives more than 1000 emails per day or otherwise exceeds the "free use" policies of the DNSBL services.
- Local DNSBL performance reduces your email server's work load and idle time waiting for public DNSBL response.
Pros and Cons of Running a Private DNSBL
- PRO: Your email server can more efficiently identify and drop connections from repeat offenders. Public DNSBLs are slower to respond.
- PRO: It makes you feel good when you can block an annoyance and they have to ask You to unblock them.
- CON: Some of your customers, suppliers, and consultants use the same email services that send spam. If not careful, you might block a spammer and your customer with the same listing. (e.g. accidentally block email from yahoo.com servers).
- CON: The Internet IP address space is BIG (even for IPv4) and the process of identifying list candidates is a tedious maintenance task.
How Does a DNSBL Work?
A DNSBL server has one or more domains with records that are structured for storing IPv4 Addresses for efficient reverse lookup within the zone.
The storage and lookup process is similar to a Reverse Lookup used to find a FQDN (Fully Qualified Domain Name) for an IP address. The difference is that a DNSBL lookup is a Forward Lookup that looks up a FQDN constructed using the reverse IP Address and the DNSBL server's domain then resolves it to an IP address. The IP addresses returned by a DNSBL are typically 127.0.0.2 to 127.0.0.254.
DNS Servers are generally light weight and high performance. A decent DNS Server can handle millions of DNSBL records and process hundreds of queries per second.
Windows Based DNSBL Implementation
Requirements
- Windows Server 2000 or later
- Microsoft DNS Server
EMail Lab Exercise - Windows Server 2012 R2, DNS Server Setup
1. Create a typical Windows Server VM with 1 Network Ethernet Adapter
2. Clean Install Windows Server 2012 R2 in a VM
3. Right-Click on the Network icon (bottom right) and Open Network and Sharing Center
4. Configure the Ethernet adapter IPv4 (your values may differ)
* IP Address: 172.30.10.53
* Subnet Mask: 255.255.0.0
* Default Gateway: 172.30.0.2
* DNS Server: 172.30.10.53 Save as the DNS Server
5. In the Server Manager, Select the Local Server
6. Configure Time Settings and Host Name, Reboot
7. In Server Manager, Click "Add Roles and Features" and install the DNS Server Role
8. Figure out how to pin the DNS Manager to the Task Bar and Start Menu for frequent access
9. Launch the DNS Server Manager, and Click the "View" menu and Check "Advanced"
Intranet DNS Server Concept
A reason for using an Intranet DNS Server is to resolve FQDNs that have Local IP Addresses. In Windows Active Directory, an Intranet DNS Server that is integrated with Active Directory is required. The DNS queries for FQDNs in non-local domains are usually forwarded to an Internet DNS server, like Google's 8.8.8.8.
DNSBL Server
A DNSBL Server is a DNS Server with one or more Forward Zones whose Type A records are for FQDNs formatted with the reverse IPv4 Address and domain. Name Server Delegations are defined in the Intranet DNS Server to enable queries to be made to the DNSBL zone without requiring the DNSBL Server to forward queries for unknown FQDNs. It is hard to explain, easier to demonstrate.
EMail Lab Exercise - Configuring the DNSBL Server
Create Forward Primary Zone for the DNSBL Domain
- NOTE: DO NOT USE YOUR MAIN DOMAIN FOR THE DNSBL DOMAIN - especially if using Active Directory!
- Our DNSBL domain name will be emaillab.net
- Our Server's Host Name is email-lab-dnsbl
1. Right click the Forward Lookup Zones and select the New Zone... menu item. 2. Create a Primary Zone named emaillab.net; finish the dialog (defaults are ok)
Create a Zone and Delegation Name Server for the DNS Black List
5. Right click the Forward Lookup Zones and select the New Zone... menu item. 6. Create a Primary Zone named dnsbl.emaillab.net; finish the dialog (defaults are ok) 7. Right Click on the emaillab.net domain and select the New Delegation... menu item. 8. Enter dnsbl for the Delegated Domain field; click Next 9. Add a Name server with FQDN = email-lab-dnsbl and Resolve IP address = 172.30.10.53 10. Finish the New Delegation wizard.
Create a Zone and Delegation Name Server for the DNS White List
11. Right click the Forward Lookup Zones and select the New Zone... menu item. 12. Create a Primary Zone named dnswl.emaillab.net; finish the dialog (defaults are ok) 13. Right Click on the emaillab.net domain and select the New Delegation... menu item. 14. Enter dnswl for the Delegated Domain field; click Next 15. Add a Name server with FQDN = email-lab-dnsbl and Resolve IP address = 172.30.10.53 16. Finish the New Delegation wizard.
Congratulations! You have completed the DNSBL Server setup!
EMail Lab Exercise - Adding DNS Records to your DNSBL Server
Add Simple Host(A) Records
First, we will add simple "spam.dnsbl.emaillab.net" and "notspam.dnsbw.emaillab.net" records so we can easily ping our DNSBL Server domains.
1. Right Click on the dnsbl.emaillab.net Forward zone 2. Add a Host(A) record for spam with IP Address 127.0.0.2 3. Repeat for the dnswl.emaillab.net Forward zone 4. Test by "ping spam.dnsbl.emaillab.net" and "ping notspam.dnswl.emaillab.net"
Observe that spam.dnsbl.emaillab.net resolves to 127.0.0.2 - your DNSBL Server is working!
Add Host(A) Records for DNSBL Formatted FQDNs
The DNSBL takes FQDNs in the reverse IPv4 format and DNSBL domain. Generally, if the DNSBL query resolves to an IP address, Spam Filters will consider the IP address "Listed" and processes the email accordingly.
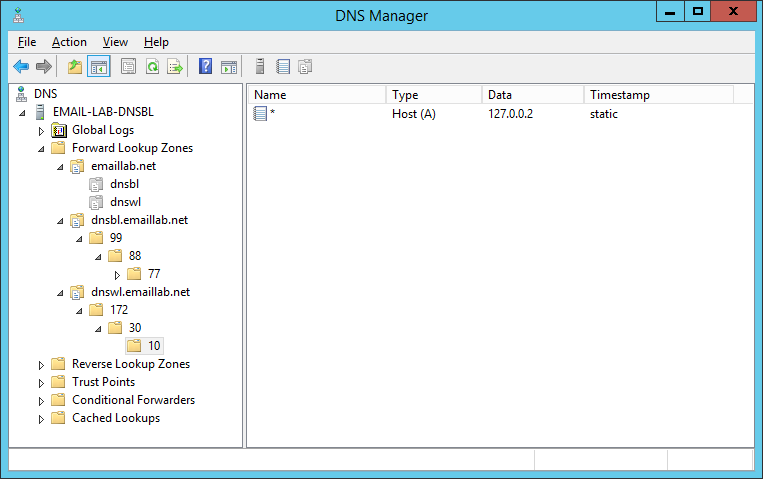
For example: IP Address 99.88.77.66 is formatted for our DNSBL as FQDN = 66.77.88.99.dnsbl.emaillab.net and we want our DNSBL Server to resolve this FQDN to 127.0.0.2
To Black List IPv4 Address 99.88.77.66 in our DNSBL do the following:
1. Right Click on the dnsbl.emaillab.net Forward zone 2. Add a Host(A) record for 66.77.88.99 with IP Address 127.0.0.2 3. Test by "ping 66.77.88.99.dnsbl.emaillab.net"
Now you know how to add a host IP address so it can be blocked by your spam filter!
Unfortunately, the IPv4 DNSBL architecture is really only designed for CIDR/24, /16, or /8 boundaries because our FQDN is constructed from the IP Address Octets. You can List entire networks by adding the .* wildcard to end of the FQDN.
For example: To White List all the IP Addresses subnet 172.30.10.0/24 do this:
1. Right Click on the dnswl.emaillab.net Forward zone 2. Add a Host(A) record for *.10.30.172 with IP Address 127.0.0.2 3. Test by "ping 22.10.30.172.dnswl.emaillab.net" and it will resolve to 127.0.0.2 4. Test any IP address in the 172.30.10.0/24 subnet and it will resolve to 127.0.0.2
DNS Data Files
Zone Data File for emaillab.net.dns
;
; Database file emaillab.net.dns for Default zone scope in zone emaillab.net.
; Zone version: 9
;
@ IN SOA email-lab-dnsbl. hostmaster. (
9 ; serial number
900 ; refresh
600 ; retry
86400 ; expire
3600 ) ; default TTL
;
; Zone NS records
;
@ NS email-lab-dnsbl.
email-lab-dnsbl. 0 A 172.30.10.53
;
; Zone records
;
;
; Delegated sub-zone: dnsbl.emaillab.net.
;
dnsbl 0 NS email-lab-dnsbl.
email-lab-dnsbl. 0 A 172.30.10.53
; End delegation
;
; Delegated sub-zone: dnswl.emaillab.net.
;
dnswl 0 NS email-lab-dnsbl.
email-lab-dnsbl. 0 A 172.30.10.53
; End delegation
Zone Data File for dnsbl.emaillab.net.dns
;
; Database file dnsbl.emaillab.net.dns for Default zone scope in zone dnsbl.emaillab.net.
; Zone version: 5
;
@ IN SOA email-lab-dnsbl. hostmaster. (
5 ; serial number
900 ; refresh
600 ; retry
86400 ; expire
3600 ) ; default TTL
;
; Zone NS records
;
@ NS email-lab-dnsbl.
;
; Zone records
;
66.77.88.99 A 127.0.0.2
spam A 127.0.0.2
Zone Data File for dnswl.emaillab.net.dns
;
; Database file dnswl.emaillab.net.dns for Default zone scope in zone dnswl.emaillab.net.
; Zone version: 7
;
@ IN SOA email-lab-dnsbl. hostmaster. (
7 ; serial number
900 ; refresh
600 ; retry
86400 ; expire
3600 ) ; default TTL
;
; Zone NS records
;
@ NS email-lab-dnsbl.
;
; Zone records
;
*.10.30.172 A 127.0.0.2
notspam A 127.0.0.2